Table of Contents
Crypto is totally anonymous, untraceable, and perfect for illicit platforms like Silk Road, right? We’ve all heard this before, but it’s actually a myth. Transactions with cryptocurrencies, including Bitcoin, are similar to posting on social media with your online username. You aren’t fully doxxed (at least you think you aren't), but you’re leaving behind permanent digital breadcrumbs that can potentially be traced back to you.
As the crypto markets have matured, blockchain analysis capabilities have also been getting better and better. In most cases, law enforcement agencies are capable of tracing cryptocurrency transactions back to individuals, and these forensic tools are only getting stronger. Privacy coins like Monero (XMR) are still fighting for true privacy, but it’s an uphill battle against regulators who believe that complete anonymity is a threat to governing laws.
In this article, we’ll look into whether cryptocurrencies are truly anonymous, or if we’re all just wearing digital masks that can easily be removed with enough effort and force.

Is the Myth of Total Anonymity in Crypto True?
Contrary to popular belief, Bitcoin isn't the online version of cash in a briefcase “hush money”. It's more akin to writing all of your financial transactions in permanent ink for public record. Why? Because every single Bitcoin transaction in history sits on the blockchain.
How did crypto and Bitcoin get this status? People often confuse anonymity with pseudonymity. Whenever someone creates a Bitcoin wallet, they’re not filling out a credit application with a social security number. Instead, they get a wallet with a mix of numbers and letters that acts as a digital pseudonym, or an online username of sorts.
It’s important to remember that Bitcoin transactions are permanent. They’re there forever on the blockchain. And if someone finds out that your wallet address belongs to you, your entire transaction history can be traced.
Ever sent funds to an exchange? Chances are that law enforcement could trace your on-chain wallet back to you if they wanted to. This is because most exchanges now require Know Your Customer (KYC) verification in order to use their services. As a result, law enforcement and regulatory bodies can now easily link on-chain identities to real-world identities.
Why Do People Seek Anonymity When Using Cryptocurrencies?
Let’s be clear about this point - privacy and anonymity aren’t bad! Most people don’t want privacy and anonymity in order to participate in illicit activities. It’s natural to want financial privacy. No one wants their neighbors to go through their bank statements and their spending history.
Protection from Censorship and State Surveillance
A big reason why people want anonymity is to avoid government overreach. Unfortunately, financial surveillance has become the norm in many regions of the world. In authoritarian regimes, the use of a privacy cryptocurrency could be what keeps someone from potentially going to jail.
Even in democratic countries, many people would frown at the idea of their financial history being tracked by the government. Financial privacy could be considered a fundamental right, similar to private conversations and medical records.
The potential of Central Bank Digital Currencies (CBDCs) has intensified such concerns. CBDCs give governments direct oversight into all transactions, and can even be used to freeze assets of those that the government persecutes.
Personal Financial Privacy in the Digital Era
Aside from government overreach, corporations also collect data about personal spending habits in order to build financial profiles. While this hasn’t happened yet, blockchain’s transparency could potentially exacerbate this form of data harvesting. Financial privacy isn’t really about hiding anything. The main focus is about maintaining autonomy in the digital era.
Illicit Use and the Dark Web: Reality vs. Exaggeration
Now you’re probably thinking - but isn’t it true that criminals and illegal platforms like Silk Road use crypto? Yes, criminals use crypto for illegal activities. What else do they use for illegal activities? Cash, encrypted messaging apps, and traditional banks. The media have often portrayed crypto exclusively as criminal tools, but the data tells a different story.

Based on Chainalysis’ report, illicit activity accounted for just 0.14% of all cryptocurrency transaction volume in 2024. Blaming crypto for criminal activity is like blaming encrypted messaging apps, or practically anything else that criminals use.
How Does Blockchain Transparency Work in Practice?
Transparency is actually a fundamental feature required for most blockchains to function. All transactions need to be verified by the network, which requires making transaction data to be publicly available. You can think of it like a bank that posts every transaction on a public website, except the names on bank accounts are replaced with pseudonyms.
For each transaction, the blockchain verifies several things. We’ll use sending Bitcoin as an example:
- You actually own the bitcoin you're sending
- You're not double-spending
- The transaction follows network rules.
The network needs to see the transaction details to validate them, which requires transparency.
As a result, the verification system creates a permanent, searchable record of every transaction. It’s possible for anyone to download the entire Bitcoin blockchain history and analyze transaction patterns to trace fund flows and identify connections between different addresses.
Different blockchains have different levels of transparency. Ethereum's account-based system allows for easy tracking of balances and transaction histories for addresses. Bitcoin's UTXO model is a slightly more complex web of transaction inputs and outputs, but can still be analyzed for patterns. All of this transparency makes blockchain analysis tools highly effective.
When we say transactions, we don’t just mean sending and receiving cryptocurrency. Transactions are all interactions on the blockchain, meaning every DeFi transaction, every NFT purchase, etc. All of this makes anonymity much more challenging.
Pseudonymity vs. Anonymity: What's the Real Difference?
Pseudonomity is posting on social media sites like Reddit under a username. Although you’re not using your real name, your posting history potentially allows others to link you to your pseudonym account.
Most cryptocurrencies function on pseudonymity. Your wallet address is your pseudonym. While your address doesn't contain any personal information, you still build up a profile of all your on-chain activities.
All it takes is one link between your pseudonym and real identity to become exposed. Use an exchange that requires KYC? That exchange knows which address is yours. Making a purchase with your crypto wallet that ships to your home address? You’ve just linked your home address with your on-chain wallet.
True anonymity, in crypto, means that transactions cannot be linked together or used to trace back to a specific user. Privacy coins such as Monero are trying to achieve exactly this. Every transaction becomes its own isolated event instead of being linked under one identity (your wallet address). By doing this, it’s much harder to build a profile of someone’s activities and track them.
Can Cryptocurrency Transactions Be Tracked?
The short answer is yes. New tools and analysis techniques are being developed everyday to make tracking easier. As the crypto markets have grown in size, blockchain analysis has also grown into a full-blown industry with sophisticated tools.
The Role of Public Ledgers and Wallet Tracking
Blockchain analysis often begins with using clustering algorithms on public ledgers (blockchains) that help identify different addresses that belong to the same user. These algorithms look for patterns. This includes addresses that transact with each other often, or are created at similar times.
Most users use only one or a handful of wallet addresses for convenience. This makes tracking even easier. Sometimes, users try to improve privacy by generating and using new addresses, but most underlying wallet software creates detectable patterns that can link addresses together
When you combine public blockchain data with off-chain information, it’s usually game over for anonymity. Exchange records, merchant databases, IP logs, social media posts, etc. can all provide additional data points that can identify the real-world individuals or entities behind pseudonymous wallet addresses.
How Blockchain Analysis Tools Identify Users
Machine learning algorithms are used nowadays by blockchain analysis companies like Chainalysis, Elliptic, and CipherTrace to analyze transaction patterns and build up profiles of wallets in order to identify suspicious activity. They're so effective that even law enforcement agencies use these tools to investigate stolen funds cases and other instances of financial crimes involving cryptocurrencies.
The blockchain analysis process usually starts with known off-chain data points, which are often provided by law enforcement, such as addresses associated with exchanges, merchants, or previously identified entities. Analysis tools are then used to trace transaction flows and identify connected addresses to build comprehensive transaction maps. These tools can even identify mixing attempts and other privacy measures.
How Do Different Blockchains Approach Privacy?
Each blockchain attracts different types of users. One key difference amongst blockchains is the level of privacy. Naturally, users with certain viewpoints on privacy will gravitate towards a blockchain with complete transparency, while another group of users will use a blockchain offering complete anonymity. The level of privacy comes with different tradeoffs involving anonymity, usability, and regulatory acceptance.
Bitcoin and Ethereum: Open by Default
The blockchain design of Bitcoin and Ethereum makes all transactions publicly visible. This, in turn, makes each network trustless as anyone is able to verify the integrity and safety of the blockchain.
This also means that there is a cost to privacy. The UTXO model of Bitcoin reveals the sender address, receiver address, and transaction amounts for each transaction. There is some added complexity as transactions can have multiple inputs and outputs.
Ethereum's account-based model functions similarly to Bitcoin. All addresses have a visible balance, and all transactions show a sender, receiver, and transaction amount. One key difference is that smart contracts exist on Ethereum. This adds even more transparency, as transactions will show which smart contract functionalities were called.
As the base layer for both chains are transparent by design, users who seek privacy typically need to use additional tools and protocols like Tornado Cash for complete privacy.
Layer 2 and Privacy Enhancements (zk-Rollups, Tornado Cash)
Layer 2 zero-knowledge rollups have been developed and built on top of the base layer of Ethereum to find a solution for privacy. These zk-rollups, such as Aztec Protocol and Polygon Hermez, allow for transaction proofs without having to reveal the sender, receiver, or transaction amounts. Essentially, transactions are guaranteed (e.g. a wallet has enough funds to send a requested amount) without needing to reveal any specifics.
Protocols like Tornado Cash allowed users to deposit Ethereum into a smart contract and then use cryptographic proofs to ensure that only the original depositor could withdraw the funds into a new address. By doing this, the connection between the original deposit and withdrawal were masked.
Ultimately, regulatory bodies cracked down on Tornado Cash. This led to controversy as the technology itself was neutral, but was associated with, and used at times for money laundering purposes.
Mixers and Tumblers: Are They Effective or Risky?
Cryptocurrency mixers and tumblers are similar to protocols like Tornado Cash, but don’t use cryptographic proofs. You deposit or send your crypto, which gets mixed with funds from other users, and then you receive the same amount of crypto to a new address that you own.
Mixers vary wildly in terms of their effectiveness against blockchain forensic tools. In order to combat these tools, sophisticated mixers will use time delays, amount randomization, and different mixing rounds. Some mixers are outright scams that steal your funds, and even legitimate mixers can potentially get your wallet address flagged as suspicious and banned from exchanges.
Which Cryptocurrencies Prioritize Privacy?
As with Tornado Cash, mixers and tumblers have gone under increased regulatory scrutiny. This has shed light back on first generation privacy coins that built privacy and anonymity into the protocol level.
Monero (XMR): Obfuscation by Design
Privacy is the default standard on Monero, where all transactions are made private. In order to accomplish this, Monero built anonymity into the protocol level through ring signatures, stealth addresses, and Ring Confidential Transactions (RingCT).
Ring signatures make it impossible to find out which input funds a transaction. This is because transactions are mixed with decoy transactions to hide the true sender.
Monero also employs stealth addresses, which means generating unique, one-time addresses for each transaction. It wouldn’t matter if your Monero address were doxxed, as incoming transactions can’t be seen since each one goes to a stealth address that only you can access.
Ring Confidential Transactions prevent blockchain analysis tools using amount-based analysis. By using cryptographic commitments, transaction amounts remain hidden, while the blockchain can still verify the transaction amounts balance correctly.
Zcash (ZEC): Zero-Knowledge Proofs in Action
Unlike Monero, Zcash users are offered a choice between either transparent or private transactions. For transparent transactions, “t-addresses” that work like Bitcoin addresses are used, while “z-addresses” using zero knowledge proofs are used for private transactions.
Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge (zk-SNARKs) are the technology power Zcash’s privacy features. You can think of it as having mathematical proof that some is able to spend a certain amount of funds, and the network can verify that this is true. This all occurs without revealing information about the sender, receiver, or the transaction amount.
Does this all sound complicated? Well, it is. The math behind zero knowledge proofs are incredibly complex, and this tech is one of the most advanced cryptography techniques in crypto. While the process is complex, the goal is simple - truly private transactions that the blockchain can verify to be true.
Zcash’s transparent vs. private optionality gives it a leg up in terms of compliance. When necessary (auditors, regulators, etc. knocking on your door), transaction details can be provided while still maintaining privacy for normal, everyday transactions.
Dash (DASH) and Other Privacy-Centric Projects
Dash originally started as a privacy-focused project. Features included PrivateSend, which used mixing to muddle transaction histories. As mentioned previously, mixers are used to disrupt the connection between inputs and outputs.
Due to the regulatory environment, many privacy-centric projects, including DASH, have shifted into new directions. Privacy projects such as Firo (formerly Zcoin), and new privacy technology like MimbleWimble protocol for confidential transactions, are still being developed. However, it’s clear that the space is not the same as it once was, when privacy coins like Monero (XMR), Zcash (ZEC), and Dash (DASH) were among the top ranked coins by market cap.
How Are Governments and Regulators Reacting to Privacy Coins?
It’s clear that governments and regulators are not fans of privacy coins. The Tornado Cash case has shown that developers of privacy protocols are not immune from heavy fines and / or jail time. This ultimately pits privacy advocates against enforcement and financial regulators.
AML, KYC, and the FATF Travel Rule
Anti-money laundering (AML) and Know Your Customer (KYC) regulations are the norm in traditional finance. Regulators want crypto to play by the same rules, which is why most centralized exchanges now require KYC.
Many people argue that the Financial Action Task Force (FATF) extended its "Travel Rule" to explicitly provide oversight of cryptocurrencies, requiring financial service providers to share customer information for transactions above certain thresholds.
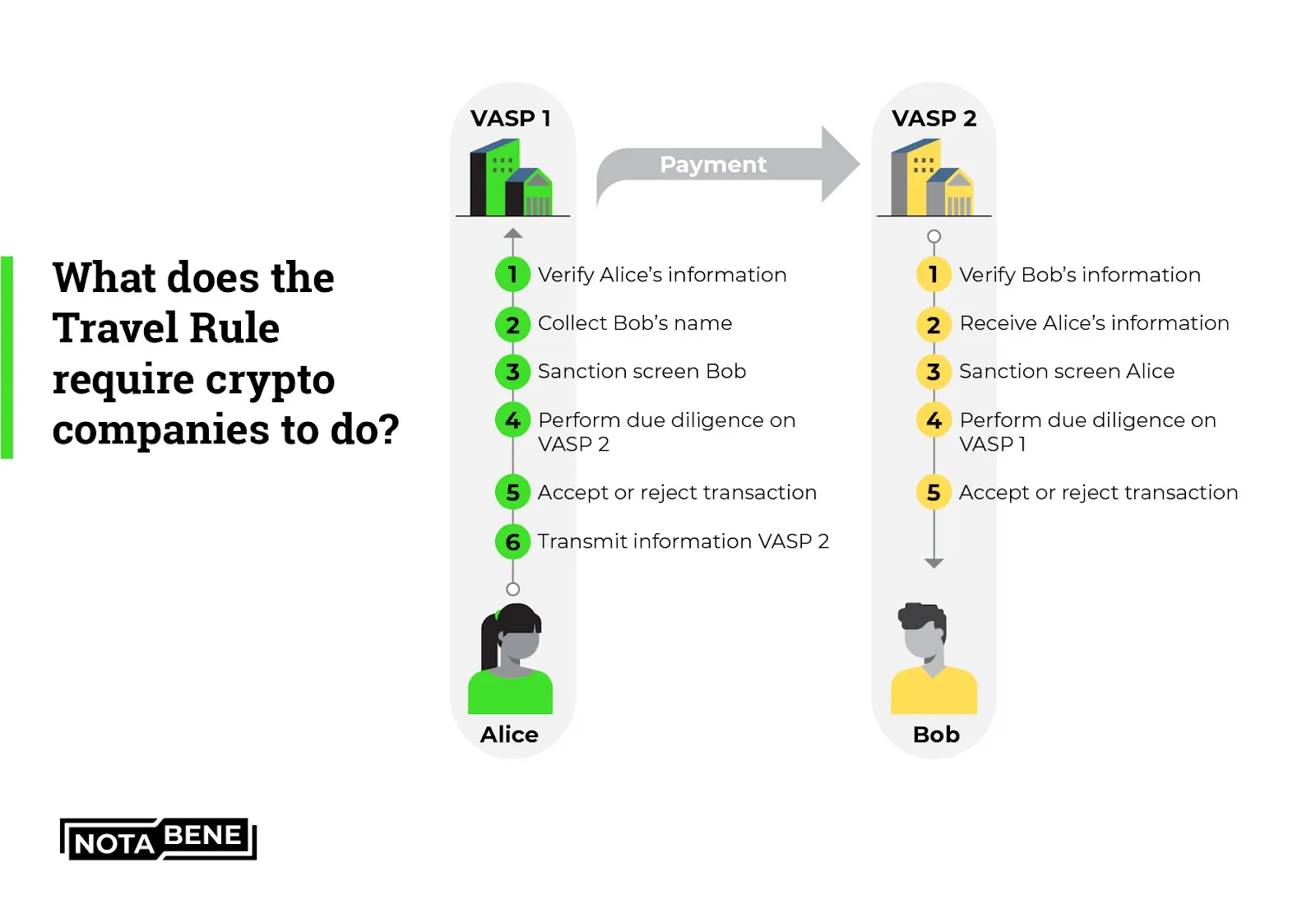
As a result, cryptocurrency service providers have either implemented enhanced monitoring for privacy coin transactions, or have avoided them completely due to the additional hassle. Often times, this has meant a complete delisting of privacy coins on exchanges due to their regulatory and operational complexity.
Bans and Trading Restrictions on Privacy Tokens
Other countries have simply opted to ban privacy coins outright. Countries including South Korea, Japan, and Australia have prohibited exchanges from offering existing, or listing new privacy coins. In the European Union, new anti-money laundering regulations will outlaw privacy coins and anonymous cryptocurrency accounts will be starting in 2027.
Major exchanges like Binance, Coinbase, and Kraken have opted to voluntarily delist privacy coins even in jurisdictions without explicit bans in order to avoid any potential future regulatory issues. All of this makes it very difficult for normal users to buy or use privacy coins.
Partnerships with Chain Analysis and Surveillance Firms
Law enforcement agencies such as the IRS, FBI, and DEA have begun using chain analysis and surveillance services from firms like Chainalysis, Elliptic, and CipherTrace. This was in response to growing financial crimes involving crypto. These partnerships have largely been deemed successes. Cases like the Colonial Pipeline ransomware attack showed that blockchain analysis can assist in recovering stolen funds and identify criminals.
Privacy coins provide a tougher challenge, as the effectiveness of blockchain analysis tools is lowered. As a result, analysis firms use other techniques, like monitoring exchange activity and other connection points when investigating cases involving privacy coins.
How Can Crypto Users Balance Privacy with Compliance?
As we mentioned earlier, there is nothing wrong with wanting privacy. Who would want a stranger to view their personal bank statements and financial records? Fortunately, there are ways to enhance privacy without breaking any laws, and while remaining compliant with regulatory bodies.
Privacy and compliance are not always mutually exclusive. Many simple operational security practices exist, which you can employ to address privacy concerns. No need to use privacy coins, or mixers and tumblers. For example, you can be careful about linking crypto activities to your real-world life (e.g. posting your wallet address on social media), and use new addresses for different transactions to better protect your personal privacy.
If you want stronger privacy protection, you will need to thoroughly understand your local laws and regulations, perhaps even with the help of a lawyer. While exchanges and financial service providers might place restrictions on privacy coins, they are still legal in many jurisdictions. As long as you meet your tax reporting duties and other legal obligations, you shouldn’t have a problem holding and using privacy coins in such jurisdictions.
Privacy also doesn’t mean anti-compliance. Many privacy advocates share required information to tax and other relevant authorities, while still maintaining privacy and protecting their information against unauthorized access. You can embrace privacy, but you’ll need to be transparent with local regulatory authorities and financial institutions when the situation calls for it.
If you’re in this category, then zero knowledge proofs may be an appealing option to watch out for. While no zk-proof solutions have hit the mainstream yet, this technology has the potential to prove compliance with regulations without revealing specific details. As an example, a person could prove that they've paid the correct amount in taxes owed on cryptocurrency gains without needing to disclose their trading history.
What Is the Future of Privacy in Crypto?
It seems unlikely that regulatory scrutiny on privacy and anonymity in crypto will subside anytime soon. However, we are seeing technological developments that could potentially satiate both regulators and privacy advocates.
Zero-Knowledge Proofs and Emerging Privacy Technologies
One such potential solution that is rapidly developing is zero knowledge proofs. This technology has the potential to verifiably prove compliance with regulations without revealing the underlying data.
Projects like Aztec Protocol and Polygon Hermez have already started to show how zero knowledge proofs are able to enable private transactions on public blockchains (Ethereum). As they continue to mature and eventually become more user-friendly, they could provide the privacy options that privacy advocates have been looking for without the scrutiny that has been placed on traditional privacy coins.
Programmable privacy through smart contracts is another rapidly developing technology that may provide a solution. With this, users could potentially have the power to control exactly what information they reveal, and to whom. For example, a user could selectively disclose information for compliance purposes, but keeping other non-necessary information private.
Many other cryptography technologies, such as bulletproofs, STARKs, and other zero knowledge proof systems continue to be developed. They offer the possibility of a future in which privacy-preserving transactions are practical for mainstream adoption.
The Debate: Is Privacy a Fundamental Right or a Security Threat?
This is a question with no right or wrong answers, and with cases to be made on both sides. Advocates for privacy equate financial privacy to private conversations and personal data, privacy to which are largely considered fundamental rights. Another point is that authoritarian regimes have historically used financial surveillance to oppress political dissidents, and gives governments unjust levels of power.
Law enforcement and regulatory agencies would argue instead that privacy should be sacrificed for the sake of preventing money laundering, terrorist financing, and tax evasion. The worry here is that anonymity enables criminal activity and undermines governing laws.
Both sides make good arguments. The trick is to find a solution somewhere in the middle. Complete transparency eliminates even basic levels of privacy, while complete anonymity eliminates accountability for bad actors. The right balance seems to be in protecting legitimate privacy concerns while preventing crime and abuse.
There is likely no one size fits all solution here. Countries have already put laws in place regarding privacy, and they’re all different. Some share similar concerns about preserving privacy and preventing corporate / government overreach, while others prioritize security and preventing crimes.
This debate will continue to have an impact on the development of future cryptocurrency and blockchain technology. If enough people and lawmakers believe that privacy is worth preserving, then we’ll continue to see innovation in technology such as zero knowledge proofs. If not, then privacy coins and mixing / tumbler services could face even further regulatory scrutiny and restrictions.
Final Thoughts: Can True Anonymity in Cryptocurrency Ever Exist?
In this article so far, we’ve gone through different technical details and the current regulatory landscape. Perhaps a deeper level question to consider though, is whether true anonymity in crypto can actually exist.
Defining “true anonymity” is a challenge in and of itself. Looking at things from a technical angle, projects like Monero have achieved success in hiding transaction details. When used correctly, the cryptographic techniques used by privacy coins make individual transactions nearly impossible to trace, at least from a technical standpoint and without additional data points.
The “without additional data points” is an important factor. Once a user interacts with a regulated exchange, or makes a purchase from a merchant that will need to collect personal information, data points are revealed that drastically lowers your anonymity. Anonymity isn’t just about technical cryptography, it also involves many things like operational security, and ultimately, regulatory acceptance.
It could simply be that complete anonymity and mainstream adoption are fundamentally at odds due to the current regulatory situation. If you never make privacy compromises, chances are that you’ll never be able to cash your crypto out using exchanges, or buy anything from online retailers. Maybe this works for an off the grid type of person, but this won’t work for most people.
As we’ve seen with countries implementing varying levels of privacy-preserving and privacy-intrusive laws, we’ll likely see different levels of privacy technologies emerge. Some may play hardball with regulators and opt for complete anonymity, while others try to work with regulators to determine which privacy features make the most sense.
As a result, we’re probably heading towards a future in which there are different shades of privacy. On one side of the scale, there are transparent but pseudonymous transactions (Bitcoin), and on the other, there is complete anonymity (Monero).
In the middle, we’re seeing privacy-enhanced solutions like zero knowledge proofs, and we’ll see more technologies develop on this scale. Users will have the ability to choose amongst these options based on their individual privacy preferences and needs, level of risk tolerance, and their local regulatory environment.
One thing that does seem clear is that there is still a strong demand for financial privacy. As personal finance becomes increasingly digital and monitored, the demand for and appeal of privacy-preserving technologies will continue to grow. This could potentially lead to better privacy tools, or more restrictive regulations. Privacy advocates and regulatory agencies can hopefully work together and agree that privacy and legitimate use can go hand in hand.
This question on true anonymity is really a broader debate and reflection on society about privacy, surveillance, and freedom in our increasingly digital world. Genuine and legitimate financial privacy can be achieved with existing, and future technologies, but this future is dependent on evolving political and social changes. Maybe the most important thing to take from this debate on true anonymity is that technology is only part of the equation.
Disclaimer: The content provided in this article is for educational and informational purposes only and should not be considered financial or investment advice. Interacting with blockchain, crypto assets, and Web3 applications involves risks, including the potential loss of funds. Venga encourages readers to conduct thorough research and understand the risks before engaging with any crypto assets or blockchain technologies. For more details, please refer to our terms of service.
