Table of Contents
Have you ever lost access to your crypto wallet? Pretty scary, right?
Surprisingly, or not, it’s often because of silly mistakes like forgotten passwords, misplaced private keys, or hardware failures.
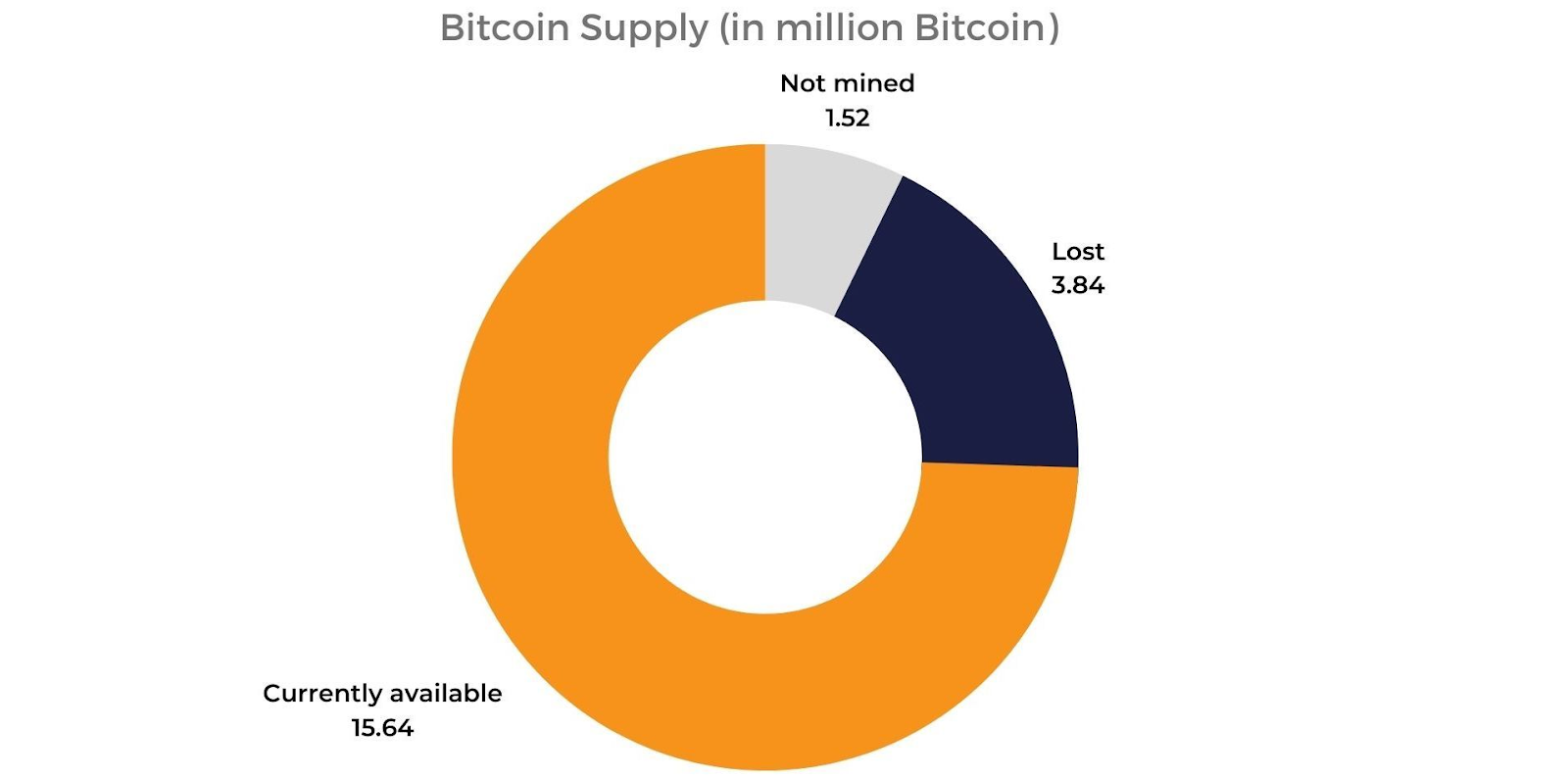
In fact, a study shows that 20% of all Bitcoin is lost due to these reasons. But don’t worry,you can save yourself from this loss by securing your crypto wallet properly.
Here’s how.
Why Is Wallet Security So Important in Crypto?
In crypto, there is no “forgot password” button or bank manager that you can call when things go sideways. Once your access is lost, it’s lost for good. That’s why wallet security is not just important, it’s your lifeline.
The Risks of Losing Private Keys or Access
Without your private key, there is no backup, no reset, and absolutely no way back in. Many people make simple mistakes that end up being their worst.
And yes, you’d be surprised to know that people really do lose a life-changing amount of crypto just because of minor mistakes.
A famous example is James Howells from the UK. Back in 2013, he accidentally threw away a hard drive that had 8,000 Bitcoins (yes, thousands), which is worth hundreds of millions of dollars today.
Once he realized this, he tried to get authorization to search the landfill, and even tried to buy it by raising money, but unfortunately, the case is now closed, and those Bitcoins are lost forever.
What Happens When Wallets Are Compromised
Now imagine a different situation. Instead of losing your access, someone else gets in. If a hacker manages to steal your private key, they can drain your wallet in seconds.
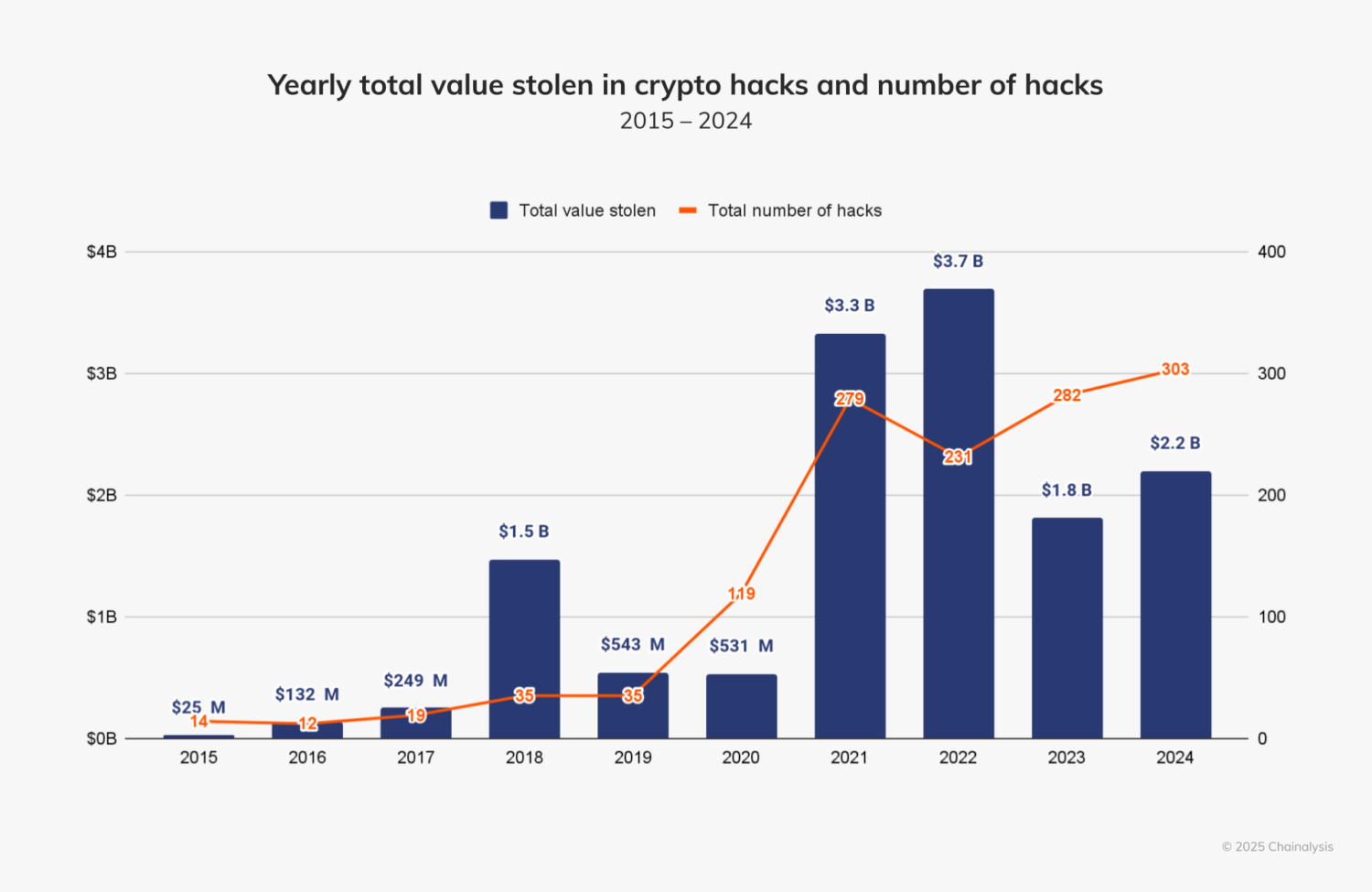
If you already are a crypto user, you know that crypto transactions are final. Once it’s done, there’s no rewind. To put this in numbers, 43.8% of the crypto that was stolen in 2024 (valued at $2.2 billion) was due to private key compromises.
Hackers don’t care about who you are, or they do but only to identify you as their target. They get your wallet access, get in, move the funds, and disappear like nothing happened. No second chances.
Which Type of Wallet Should You Use?
The first step to protecting your funds is to choose a crypto wallet that actually keeps them secure and matches your needs. Let’s take a look at how different wallets work, so you know which one is best for you.
Hot vs. Cold Wallets: Pros and Cons
A general rule of thumb? It’s recommended to use a hot wallet for small amounts or frequent transactions while keeping the bulk of your funds in cold storage crypto wallets.
Here’s a side-by-side comparison for a quick peek.
*Think of hot wallets like a regular wallet in your pocket, but not where you keep all your life savings. Cold wallets are more like a safe at home.
2. Custodial vs. Non-Custodial Wallets: Who Controls Your Funds?
Simply put, a custodial wallet is managed by a company or exchange. They hold your private keys for you, which can be very convenient especially if you’re a beginner or a trader.
The only problem is if the exchange gets hacked or collapses, your money can evaporate. Remember the crash of FTX in 2022? Billions of dollars just gone because users trusted the wrong exchange. So, always choose reliable platforms.
Non-custodial wallets are different. Here, you control your keys. That means full independence and no reliance on third parties, but that also means you have to keep them secure yourself.
The famous crypto phrase “Not your keys, not your coins” comes from this difference. But with freedom comes responsibility. If you lose your seed phrase, there’s no company to call and no way to recover your funds.
What Are the Different Types of Attacks on Crypto Wallets?
Crypto wallets give you full control over your money. However, that control also comes with responsibility. Hackers are getting smarter and they know how to exploit the weak points and look for small mistakes.
When you know which types of attacks are common on crypto wallets, you’ll be more vigilant. So, here are the ones you should be aware of.
1. Social Engineering
Social engineering attacks rely on manipulating human behavior rather than hacking technology directly. In this attack, hackers usually pose as trusted sources and send emails or messages that look legitimate and have an irresistible offer.
They can also create fake websites that look exactly like the real ones. And people mostly end up adding their secret phrase in hopes of getting that 1 ETH they are promised out of nowhere.
Studies show that 98% of cyberattacks involve social engineering in some form. So, if you ever get a call or email asking for sensible information or an action you didn’t initiate, be cautious and don’t tap on any links. Always double check the sender or the domain first.
2. Malware and Keyloggers
Malware and keyloggers are malicious programs that silently record your keystrokes or capture sensitive information stored on your device. They can be installed through suspicious downloads, fake apps, or phishing links.
Once activated, malware can steal private keys or passwords without you even noticing it before your funds are gone. In 2024, crypto wallet malware attacks contributed to losses totaling $494 million.
3. SIM Swapping
SIM swapping attacks target your phone number, often to bypass two-factor authentication (2FA). Hackers impersonate you to your mobile carrier and get your number transferred to another SIM card that they control.
This way, the hackers can intercept any 2FA codes sent via SMS and log into your accounts. The FBI reported $26 million in losses due to SIM swapping in 2024. So, make sure your account doesn’t just rely on SMS-based authentication.
How to Back Up Your Wallet Safely
It’s up to you whether you want to keep sniping those memecoins or sit in a corner thinking about how you could have backed up the key phrase when you had the chance. Here’s how you can do it:
1. Storing Seed Phrases Offline
When you create a crypto wallet, you get a 12 to 24-word seed phrase (it’s like a very strong password to access it). The easiest way you can keep it safe is by writing it down on paper or storing it on a metal backup plate.
Why? Because offline storage cannot be hacked.
The wallet can only be accessed if someone somehow gets possession of this seed phrase, so keeping it offline removes the risk of losing your private key in cyber attacks.
2. Using Multiple Backup Locations
You should never store your backup in a single location. It’s risky. The smart choice is to create multiple backups and keep them in different places.
Just like the saying goes, “never put all the eggs in one basket.” If one copy is destroyed somehow, you still have another to fall back on.
3. Why Screenshots and Cloud Storage Are Unsafe
It might feel easier just to take a screenshot and move on with your life. However, it’s surprisingly one of the fastest ways to lose your funds. Hackers often target cloud storage and personal devices because they know many people keep sensitive data there.
In fact, a 2025 Verizon Data Breach Report found that over 88% of hacking-related breaches involve stolen credentials from cloud or device access. If someone gets hold of your screenshot, your wallet is as good as gone.

How to Strengthen Account Security
Backing up your wallet is just one part of the puzzle. You also need to lock down the doors that hackers use to break in. A few smart habits can make your wallet far harder to compromise and save you from losing access to your crypto.
1. Enabling Two-Factor Authentication (2FA)
Two-factor authentication (2FA) might seem useless to some, but it’s highly effective. Microsoft itself reported that 2FA prevents attacks 99.9% of the time. So, instead of just using your password, also use a one-time code from an app like Google Authenticator.
This might sound basic, but it’s one of the best ways to block most unauthorized access attempts.
2. Creating Strong, Unique Passwords
Your wallet password is the fine line of defense. If you’re creating an account on an exchange, never use short or repeated passwords as they can be cracked easily.
Always aim for a long password with symbols, letters, and numbers, and keep that saved on paper too. You can also use a password manager to generate and store your password..
3. Recognizing Phishing Attempts and Scams
Phishing is one of the most common ways wallets are compromised. Hackers send fake emails, create copycat websites, or even build malicious apps to trick you into handing over your login credentials or seed phrase.
Don’t forget to double-check website URLs and never share your private keys with anyone (a simple behaviour that you adopt at all times).
It’s also supported by facts that show that phishing was the top cybercrime in 2024, which cost victims more than $53 million in losses.

How to Protect the Devices You Use for Crypto
Think about it this way: even the strongest vaults are useless if the door is wide open. The same applies here, but the door here is your phone or laptop.
So, let’s see how you can keep your tech locked away from the hackers.
1. Keeping Software and Firmware Up to Date
Yes, updates pop up at the worst time. But skipping them is like leaving your front door unlocked because it’s "inconvenient" to always think about the keys. Bad idea.
Outdated software is one of hackers’ favorite entry points. Studies show that nearly 60% of breaches in 2022 were tied to unpatched software. So, whatever you’re doing, hit that update button if you want to secure your wallet.

2. Using Antivirus and VPN for Extra Protection
Antivirus is like your digital guard dog, and VPN is your invisibility cloak. Together, they make life much harder for hackers.
With over 450,000 new malware programs showing daily (yep, daily), having both is no longer a plus but a must. A good antivirus keeps your device clean meanwhile a VPN keeps your online traffic private.
Why You Should Avoid Public Wi-Fi for Wallet Access
Public Wi-Fi is basically a hacker’s playground. They are unsecure, which makes them super easy for someone to peek at your connection.
Forbes even wrote an article on it and reported that 40% of people who used public Wi-Fi had their info compromised. That’s literally almost half of everyone you see sipping lattes while scrolling.
When it comes to crypto, stick to your private home network or, at the very least, use a VPN if you’re out.
Your coffee can be public, but your wallet access? Never!
What Should You Do If You Lose Access to Your Wallet?
Losing access to your crypto wallet can feel like your heart just dropped into your stomach. But don’t panic, you can still recover it if you’ve prepared the right way. The trick is knowing your options before things go wrong.
1. Recovering Funds from a Backup Phrase
Your seed phrase is the master key to your wallet. If you lose your device, you can simply enter the phrase into a new wallet app or hardware wallet to get everything back. Think of it like having a spare key to your house.
But without proper backup, things can still go wrong. And you wouldn’t want to be part of the holders who, in total, lost 20% of the Bitcoin supply due to simply misplacing their private keys. That’s billions gone. Don’t let that be you.
2. How Custodial Wallet Support Can Help
If you’re using a custodial wallet (where a company holds the keys for you), you’ve got a safety net. Most providers have recovery processes in place, including identity verification and support teams.
It’s like calling your bank if you forget your password. Just know the trade-off: you’re trusting them with your funds. Still, for beginners or busy users, that safety cushion is convenient.
3. Setting Up a Recovery Plan in Advance
Here’s where future-you will thank present-you. Write down your recovery steps clearly, store your backups in more than one secure location, and if you trust someone completely, let them know how to access them if something happens to you.
It might feel like overkill, but it’s better than scrambling later. Remember, in crypto, there’s no “forgot password” button. A little planning now can save you a lot of headaches later on.
Conclusion: Be Your Own Bank But Secure It First
Crypto gives you the freedom that traditional banks can’t match. You are in complete control of your money, anytime, anywhere. But with that freedom comes big responsibility as there’s no support desk waiting to bail you out if something goes wrong.
Your wallet security is on you..
Just think of it this way: you wouldn’t leave your house unlocked, so why leave your digital money unprotected?
Be your own bank, but secure it first. And if you don’t want the responsibility of keeping your seed phrase secure yourself, you can always use an exchange, but a trusted one.
FAQs
1. Can I recover my crypto if I forget my wallet password?
If you’re using a non-custodial wallet, then there’s nothing you can do without a backup. However, if you trust and use custodial wallets, you can reset your account’s password through support and get back into your wallet.
2. Can I use the same crypto wallet on multiple devices?
Yes, you can easily sync a crypto wallet on multiple devices by using your recovery phrase. However, every extra device increases risk if it’s not secured. Only install wallets on devices you trust and always enable additional security measures, such as two-factor authentication (2FA) or biometric locks.
3. Should I use biometric locks (like fingerprints) for wallets?
Biometrics add a level of convenience, but they shouldn’t replace strong passwords or backups. Hackers can even bypass fingerprints or facial recognition with advanced tools. So, use these as an extra barrier, but never rely on them as your only line of defense. Strong keys and phrases still matter most.
4. Are browser extension wallets safe to use?
Browser wallets, such as MetaMask, are popular but carry risks since they’re online. Phishing sites, fake extensions, and malware are common threats. They’re fine for small amounts or daily use, but for larger holdings, prefer a hardware or offline storage.
Disclaimer: The content provided in this article is for educational and informational purposes only and should not be considered financial or investment advice. Interacting with blockchain, crypto assets, and Web3 applications involves risks, including the potential loss of funds. Venga encourages readers to conduct thorough research and understand the risks before engaging with any crypto assets or blockchain technologies. For more details, please refer to our terms of service.
